Setting up LDAP authentication in Moodle LMS is a great way to enable single sign-on, the synchronization of user accounts with other systems in your organization. Once you have configured the LDAP authentication plugin in Moodle and confirmed that it is working and you can log in, don't forget to enable LDAP User Sync to keep your user account status in sync.
When first setting LDAP up, you may not realize that it may be bringing more accounts into Moodle than you expected like workstations, printers, and other devices which may be attached and logged into your network through Active Directory (AD). The trick is to filter synchronization of user accounts coming from AD to just persons of class users by completing the following steps:

- Go to Site Administration > Plugins > Authentication > Manage Authentication. Be sure to enable LDAP Server in the list if it is disabled by clicking on the related icon in the Enable column.
- Use the Settings link to open the configuration page for LDAP Server. If this is the first time you are setting up LDAP, contact your LDAP/Active directory administrator. They should know most of the information that you will need to fill out on this page.
- Scroll down to the User Lookup Settings section.
- Set User Attribute to: sAMAccountName
- Set Object class to: (&(objectCategory=person)(objectClass=user))
- Save.
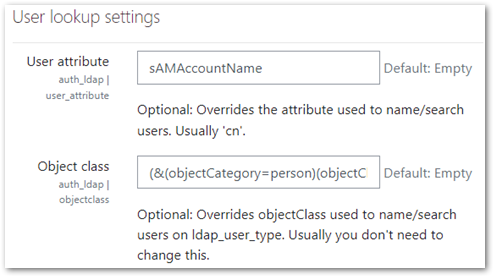
The Object class field name in Moodle is a little misleading. One might initially think that you should use it to just give Object class a value when it is more of a field to specify filters. In this case, specifying an object category of person and an object class of user will filter out non-user accounts like workstations, printers and other devices which may be attached and logged into your network through AD.
Account usernames in Active Directory may contain more types of characters than Moodle allows by default. For example, you may also have AD usernames that start with a "$" (dollar sign) or "#" (hashtag/pound sign) which simply should not be there for valid usernames. You can fix this by adding more filters to the Object Class setting:
(&(objectCategory=person)(objectClass=user)(!(sAMAccountName=$*))(!(sAMAccountName=#*))(!(userAccountControl:1.2.840.113556.1.4.803:=2))(!(userAccountControl:1.2.840.113556.1.4.803:=32))(!(userAccountControl:1.2.840.113556.1.4.803:=65536)))
Here is an explanation of this does:
- (& means all of the following must match (AND them together).
- (objectCategory=person) : The object category must be a "person"; AND
- (objectClass=user) : The object class must be a "user"; AND
- (!(sAMAccountName=$*)) : The sAMAAccountName (the username) must not (!) start with a dollar ($) symbol followed by any number of characters (*); AND
- (!(sAMAccountName=#*)) : The sAMAAccountName (the username) must not (!) start with a hash tag (#) symbol followed by any number of characters (*) ; AND
- (!(userAccountControl:1.2.840.113556.1.4.803:=2)) : The userAccountControl:1.2.840.113556.1.4.803 (user account) must not (!) be disabled (:=2); AND
- (!(userAccountControl:1.2.840.113556.1.4.803:=32)) : The userAccountControl:1.2.840.113556.1.4.803 (user account) must not (!) not be required to have a password (:=32); AND
- (!(userAccountControl:1.2.840.113556.1.4.803:=32)) : The userAccountControl:1.2.840.113556.1.4.803 (user account) must not (!) be set to Password does not expire (:=65536);
- ) is to close the initial (&.
Modify this to suit your organization's password policy. If you run into problems, it will often be the result of unbalanced ( and ) parentheses. It could also be that you are trying to filter out a character with a special meaning in which case you will need to escape the character by preceding it with a backslash (\). For more information about the types and syntax of filters that you can use, see Active Directory: LDAP Syntax Filters.
The result is that the filter will exclude user accounts that do not meet the filter's criteria. If you set the Removed ext user LDAP setting in Moodle to Suspend internal, Moodle will automatically suspend any user accounts which have been filtered out by the LDAP synchronization process thanks to the additional filters.
WARNING: Your site may become less or non-responsive during the synchronization process. Do the following off-hours or work this out on a different instance of Moodle.
You should be able to run the LDAP synchronization process manually from within Moodle by going to Site Administration > Server > Scheduled Tasks. Scroll down to the LDAP users sync job. You should see a small link called "Run now". Use this link to run the LDAP synchronization process manually.

If you don't see the link, you will need to go to Site Administration > Server > System Paths and set the Path to PHP CLI field to enable the Run Now link. You may also need to go to Site Administration > Security > Site Security Settings to enable the Allow 'Run now' for Scheduled Tasks setting.
If your legitimate account usernames include characters with accents or Asian script characters, you will also need to tell Moodle to allow special characters outside the normal a-z, A-Z range. You can do this by navigating to Site Administration > Security > Site Policies and enabling Allow extended characters in usernames. This should only be done if you are sure that accounts in AD which contain special characters are valid active user accounts. I've seen some Active Directory administrators rename users to johndoe(old) instead of disabling the account. By allowing extended characters in usernames, you could be propagating a security risk to your Moodle site and possibly inadvertently creating enabled user accounts that should not exist in Moodle
Did you know? Prior to Moodle 4.0, the synchronization process aborted on the first LDAP synchronization error, regardless of the reason. A patch described in MDL-58395 has been integrated as of Moodle 4.0 but will need to be applied manually to previous versions. This patch does three very important things to help you troubleshoot sync issues:
- It displays the user's information for the account that are causing LDAP sync issues.
- It changes the script behaviour to continue the process if there is a problem with a particular account so that, at least the rest of the accounts are hopefully properly synchronized.
- It provides a summary at the end to let you know if there was a problem so that you don't need to scroll through the whole list of accounts being created/synchronized to find the odd ones that didn't work -- if there are any. As you might imagine, failing to sync all accounts if the first in the list fails could result in a serious security issue.
Hope you found this information useful. Share your experience in implementing Moodle LMS in the comments below.
Contact us if you have any questions or concerns.
Michael Milette
TNG Consulting Inc.
www.tngconsulting.ca





Add a comment: